Spam Checks
SmarterMail comes equipped with a number of antispam features and functions that allow you to be as aggressive as you want when combating spam. Default antispam settings were configured during installation, but these settings can be modified at any time.
Due to the flexible nature of SmarterMail's antispam setup, spam checks can influence the spam decision as much or little as you want. Each spam check has one or more associated weights. When spam protection runs on an email, all enabled spam checks are performed. The total weight of all spam checks is what comprises the final spam weight for the email. A spam probability level (Low, Medium or High) is then assigned to the email using the weights configured by the system administrator on the Filtering card of the Options tab. Based on the email's total spam weight / probability of being spam, the corresponding spam filtering action is taken.
An added benefit to SmarterMail's antispam administration is the ability to combat both inbound and outbound spam messages. Most mail servers only allow administrators to keep spam from entering the mail server. SmarterMail helps protect mail users from inbound spam and also includes the added benefit of keeping mail servers from actually sending spam, thereby helping to protect the mail server from being blacklisted.
The Spam Checks, RBLs and URIBLs tabs can be used to create or modify existing spam checks and RBLs for the system.
- Cyren IP Reputation
- Cyren Premium Antispam
- Declude
- DKIM
- Honey Pot
- Message Sniffer
- Null Sender
- Remote Rspamd
- Remote Spam Assassin
- Reverse DNS
- SpamAssassin-based Pattern Matching
- SPF
- Creating Custom Rules
Spam Checks
The Spam Checks tab shows all non-RBL/non-URIBL checks that are performed on a message. These checks can include licensed add-ons such as Message Sniffer, as well as standard checks such as DKIM, SPF and more. Any of these checks can be enabled or disabled for Inbound and/or Outbound SMTP, and each can be edited or removed. To edit a check, simply click it to open its settings. To add a new Spam Check, such as adding in an antispam appliance, click the New button.
SmarterMail includes several spam checks by default. Each check is described in detail, below.
In general, one or more of the following options may be available when creating a custom spam check or modifying an existing one:
- Enable Spool Filtering - When enabled, the weight assigned for the spam check is added to the message and used as part of its overall spam score. SmarterMail then handles the message based on the spam settings configured for a domain.
- Enable Inbound SMTP blocking - This option is used in conjunction with the SMTP Blocking settings configured in Antispam Options. When enabled, this spam check is counted toward the weight threshold for the blocking of inbound emails. As SMTP blocks are done at the IP level and not based on message content, some spam checks do not offer SMTP blocking. If this option is not available, then that particular spam check does not offer SMTP blocking and must rely on content filtering instead.
- Enable Outbound SMTP blocking - This option is used in conjunction with the SMTP Blocking settings configured in Antispam Options. When enabled, this spam check is counted toward the weight threshold for the blocking of outbound emails. As SMTP blocks are done at the IP level and not based on message content, some spam checks do not offer SMTP blocking. If this option is not available, then that particular spam check does not offer SMTP blocking and must rely on content filtering instead.
- Weight - The weight range available for the spam check. Each spam check may utilize unique spam weight options.
Cyren IP Reputation
Cyren IP Reputation builds upon what existing RBLs and URIBLs provide by handling the vast gray area of IPs and IP sources that have little or no information. For example, machines that are hijacked and used by botnets that dynamically use, and abuse, the innocuous IP addresses on those hijacked machines. Cyren analyzes hundreds of millions of messages every day, so they are able to classify (and re-classify), in real-time, the reputation of each IP source.
Cyren evaluates an IP, then returns to SmarterMail a "Risk Score". Cyren also categorizes IPs in what they call "Class Groups". These groups represent a composite value based on whether an IP is a high volume IP (i.e., has a substantial volume history), is a transitory or low volume IP, or if there is an IP that has a "fixed decision" regardless of its volume (e.g., whitelisted or blacklisted sources.) SmarterMail then uses these values and classifies the score as Good (or no risk), Low risk, Medium risk, or High risk.
- Enable Spool Filtering - See above for details.
- Enable Inbound SMTP Blocking - See above for details.
- Good Weight - Defaults to 0. Based on the Class Group from Cyren, these are IPs that have high volume but low risk or are whitelisted IPs PLUS their overall risk score is 0.
- Low Weight - Defaults to 0. The risk score from Cyren is 79 or below.
- Medium Weight - Defaults to 5. The risk score from Cyren is between 80 and 89.
- High Weight - Defaults to 10. The risk score from Cyren is 90 or above.
Cyren Premium Antispam
The Cyren Premium Antispam add-on is a service that uses Recurrent Pattern Detection (RPD) technology to protect against spam outbreaks in real time as messages are mass-distributed over the internet. Rather than evaluating the content of messages, the Cyren Detection Center analyzes large volumes of internet traffic in real time, recognizing and protecting against new spam outbreaks the moment they emerge. Cyren then categorizes messages as Confirmed, Bulk, Suspect, Unknown, or None.
This add-on can be purchased directly from the SmarterTools website by logging into your account and adding it to any SmarterMail license.
- Enable Spool Filtering - See above for details.
- Enable Inbound SMTP Blocking - See above for details.
- Confirmed - Defaults to 20. The message is confirmed as being spam.
- Bulk - Defaults to 10. The message is categorized as bulk mail, so it's likely spam.
- Suspect - Defaults to 10. The message is suspicious and likely either bulk email or spam.
- Unknown - Defaults to 0. Cyren is unable to categorize the message as there's not enough data.
- None - Defaults to 0. The message was not scored by Cyren, so it's likely legitimate.
Declude
Declude integration allows you to use Declude products in conjunction with the SmarterMail weighting system. Declude addresses the major threats facing networks, and are handled by a multi-layered defense. Configuration of Declude is done through the Declude product, so all you need to do in SmarterMail is enable the spam check and the Declude score will be included when calculating the total spam weight of a message. For more information, visit the Mail's Best Friend website as they currently manage and support Declude and the "Declude Reboot" product.
- Low Spam Weight - The weight that will be assigned if Declude determines a low probability of spam.
- Medium Spam Weight - The weight that will be assigned if Declude determines a medium probability of spam.
- High Spam Weight - The weight that will be assigned if Declude determines a high probability of spam.
DKIM
DKIM is an email authentication systems designed to verify the DNS domain of an email sender, and the authenticity of a sender as well as the sender's message. DKIM is the combination of Yahoo's Domain Keys and Cicso's Identified Internet Mail (IIM) standard.
- Enable Spool Filtering - See above for details.
- Pass Weight - Indicates that the email sender and message integrity were successfully verified (less likely spam). The weight you set may be 0 (for no effect) or a negative number, thereby reducing the spam rating.
- Fail Weight - Indicates that the email sender and message integrity verifications failed (most likely spam). Set this to a relatively high weight, as the probability that the email was spoofed is very high.
- None Weight - Indicates that there was not a valid DomainKey/DKIM signature found to validate the sender and message integrity. Except in very special circumstances, leave this set to 0.
- Max message size to verify (MB) (0 = Unlimited) - The maximum inbound message size you want the mail server to verify.
Honey Pot
A "honey pot" spam check derives its name because implementing it can attract spammers — or, more likely, spam bots — like "bees to honey." Basically, a system administrator populates the honey pot spam check with email addresses that are designed to be seen by, or otherwise used by, spammers. These addresses can be commonly used addresses that spammers will automatically target such as admin@your-domain.com, info@your-domain.com, hr@your-domain.com, etc. These types of addresses are commonly targeted, but SHOULD NOT be addresses that are actually used by any user of a given domain. You don't want to add admin@your-domain.com IF that is an actual address used BY a user on that domain. In fact, any addresses added as honey pot addresses DO NOT need to be an actual users. So if you DO use admin@yourdomain.com as a honey pot address, you do NOT need to add that as an actual user TO the domain. In addition, there's no limit to the number of addresses you can add. It's totally up to the system admin.
Another common way to instantiate a honey pot spam check is to add a hidden email address to a form used on a website. Spambots can scrape email addresses from these forms, then populate spam lists that are used by, or potentially sold to, spammers. By adding in a hidden (using CSS) honey pot email address to a form, you can essentially trick these bots into scraping that email address, then block any sender who uses the address.
Regardless of HOW you set your trap, honey pots can be a simple, yet effective, way of finding, scoring and then disposing of email spam for your users as well as blocking sending IP addresses.
- Enable Spool Filtering - See above for details.
- Reject found entries at SMTP level - Enabling this will automatically reject the message prior to it being delivered if the IP of the sending mail server has already been listed.
- Pass Weight - The weight you set may be 0 (for no effect) or a negative number, thereby reducing the spam rating. (Setting negative numbers is not recommended.)
- Listed Weight - This is the weight that is assigned to a message sent from an IP address that was already part of the honey pot.
- Triggered Weight - This is the weight that is assigned to a message that is sent to one of your Honey Pot Addresses. The email address must match one in the list of Honey Pot Addresses for this weight to be added to the message.
- Honey Pot Addresses - These are the actual, full email addresses you're targeting for use by spammers. For example, generic email addresses can be used such as info@example.com or contact@example.com.These should NOT be actual email addresses that are used by anyone on any domain. Ideally, they're addresses that are general enough that spammers would target them with blanket spam attacks, but not addresses that are posted anywhere or used to actually send email. They are explicitly to be used ONLY for trapping potential spammers.
Message Sniffer
The Message Sniffer add-on is an intelligent antispam scanner that uses advanced pattern recognition and collaborative learning technologies to accurately identify spam, scams, viruses, and other email borne malware before it gets to a user's mailbox.
This add-on can be purchased directly from the SmarterTools website by logging into your account and adding it to any SmarterMail license.
- Enable Spool Filtering - See above for details.
- Enable Outbound SMTP Blocking - See above for details.
- Confirmed Weight - The weight that will be assigned if Message Sniffer determines the message as coming from known spam sources.
- None Weight - The weight that will be assigned if Message Sniffer deems the message is not spam.
Null Sender
A common spam technique is to send messages with missing, or "Null" sender values in the return path. That means that the message appears to come from no one as the return path is blank. This check allows you to assign a spam weight to messages that meet this criteria.
- Enable Spool Filtering - See above for details.
- Enable Outbound SMTP Blocking - See above for details.
- Weight - The weight assigned to messages that fail this check.
Remote Rspamd
Rspamd is a fast, free, and open-source spam filtering system that, as a Linux distribution, requires installation on a remote system. However, it ties in nicely with SmarterMail. For information on setting up a remote Rspamd server, see this knowledgebase article: Deploying Rspamd For Use With SmarterMail.
- Enable Spool Filtering - See above for details.
- Enable Outbound SMTP Blocking - See above for details.
- Scoring Factor - Instead of attaching weights, like other checks, Rspamd uses a “scoring value” to normalize the value used when weighing results. This normalization takes the raw score and multiples it by a Scoring Factor (that is fully customizable) to come up with a final spam score.
- Client Timeout (seconds) - The timeout that SmarterMail will impose on a server if it cannot connect.
- Max Attempts per Message - The number of times SmarterMail will attempt to acquire an Rspamd score for an email.
- Failures Before Disable - The number of times a remote Rspamd server can fail before it is disabled.
- Disable Time (minutes) - The length of time before the Rspamd server is re-enabled.
Remote SpamAssassin
SpamAssassin itself is a powerful, third party open source mail filter used to identify spam that can be easily used alongside SmarterMail. It utilizes a wide array of tools to identify and report spam. By default, SpamAssassin will run on 127.0.0.1:783. For more information, or to download SpamAssassin, visit spamassassin.apache.org.
SmarterMail can use SpamAssassin with its weighting system:
- Enable Spool Filtering - See above for details.
- Enable Outbound SMTP Blocking - See above for details.
- Scoring Factor - Instead of attaching weights, like other checks, Remote SpamAssassin uses a “scoring value” to normalize the value used when weighing results. This normalization takes the raw score and multiples it by a Scoring Factor (that is fully customizable) to come up with a final spam score.
- Client Timeout (seconds) - The timeout that SmarterMail will impose on a server if it cannot connect.
- Max Attempts per Message - The number of times SmarterMail will attempt to acquire a SpamAssassin score for an email.
- Failures Before Disable - The number of times a remote SpamAssassin server can fail before it is disabled.
- Disable Time (minutes) - The length of time before the SpamAssassin server is re-enabled.
- Header Log Level - The amount of information SpamAssassin inserts into the header of the message
Reverse DNS
Reverse DNS checks to make sure that the IP address used to send the email has a friendly name associated with it.
- Enable Spool Filtering - See above for details.
- Enable Inbound SMTP Blocking - See above for details.
- Weight - The default weight for this spam check. If an email sender does not have a reverse DNS entry, this is the value that will be added to the message's total spam weight.
- Forward Confirm Fail Weight - Forward Confirm Reverse DNS means that an hostname has both forward and reverse DNS entries that utilize the same IP address. Using this check, SmarterMail checks the rDNS and fDNS and if there is no A record, the check fails.
- Forward Confirm Mismatch Weight - Using this check, SmarterMail checks the rDNS and fDNS and if the IPs exist, but don't match, the check fails.
SpamAssassin-Based Pattern Matching
SmarterMail includes a proprietary pattern matching engine built upon the SpamAssassin technology as part of the default installation of the product. It includes a number of spam detection techniques, including DNS-based and fuzzy-checksum-based spam detection, Bayesian filtering and more.
- Enable Spool Filtering - See above for details.
- Enable Outbound SMTP Blocking - See above for details.
- Scoring Factor - Instead of attaching weights, like other checks, a “scoring value” is used to normalize the value used when weighing results. This normalization takes the raw score and multiples it by a Scoring Factor (that is fully customizable) to come up with a final spam score.
- Header Log Level - The amount of information the pattern matching engine inserts into the header of the message. For example, a line in the header would look like the following: X-SmarterMail-SpamDetail: 2.0 BASE64_LENGTH_79_INF base64 encoded email part uses line length greater than 79 characters.
- Score only - This only adds the numeric value of the returned check to the header. In the above example, that would be "2.0"
- Score with test name - This adds the numeric value and the test name to the header. In the above example that would be "2.0 BASE64_LENGTH_79_INF"
- Score with test name and description - This adds all of the information returned: score, test name, and test description. In the above example, that would be the entire line: "2.0 BASE64_LENGTH_79_INF base64 encoded email part uses line length greater than 79 characters"
SPF (Sender Policy Framework)
SPF is a method of verifying that the sender of an email message went through the appropriate email server when sending. Therefore, as it's verifying the sending server, SPF is set up by the sending server's system administrator or the domain owner as a DNS record. (More information can be found at DMARC Analyzer.) As more and more companies add SPF information to their domain DNS records, this check will prevent spoofing at an increasing rate.
Just as with RBL/URIBL lookups, SmarterMail has a built-in 15-second timeout that will prevent excessively long SPF lookups to occur, which can impact email delivery.
- Enable Spool Filtering - See above for details.
- Enable Inbound SMTP Blocking - See above for details.
- Scan From header instead of Return Path - Enabling this means the check will use the From address for the SPF check as opposed to the message's RETURN-PATH, which is where NDRs (bounce messages) are sent. Many times spammers will spoof messages by changing the From address to make it appear like a message is coming from a legitimate person/organization even though the RETURN-PATH may be for the actual source of the message. While it is possible to spoof a message's RETURN-PATH, spoofing the From address is a much more common method used by spammers.
- Pass Weight - Indicates that the email was sent from the server specified by the SPF record (more likely good mail). The weight you set may be 0 (for no effect) or a negative number, thereby reducing the spam rating.
- Fail Weight - Indicates that the email was sent from a server prohibited by the SPF record (highly likely spam). Set this to a relatively high weight, as the probability that the email was spoofed is very high.
- SoftFail Weight - Indicates that the email was sent by a server that is questionable in the SPF record. This should either be set to 0 or a low spam weight.
- Neutral Weight - Indicates that the SPF record makes no statement for or against the server that sent the email. Except in very special circumstances, leave this set to 0.
- PermError Weight - Indicates that there is a syntax error in the SPF record. Since SPF is relatively new, some domains have published improperly formatted SPF records. It is recommended that you leave this at 0 until SPF becomes more widely adopted.
- None Weight - Indicates that the domain has no published SPF record. Since SPF is relatively new, many legitimate domains do not have SPF records. It is recommended that you leave this at 0 until SPF becomes more widely adopted.
Creating Custom Rules
Custom spam rules can be created based on the header, body text or raw content of a message. For example, BestAZLawFirm.com, which is hosted on a SmarterMail server, constantly receives important emails from the "VeryImportantClientDomain.net" domain, which is hosted on an external server. However, VeryImportantClientDomain.net is constantly getting listed on one or more blacklists because it is hosted on a mail server that isn't using properly vetted and cleansed IP addresses. To bypass any potential negative spam score senders from this domain receive when their messages hit SmarterMail, the SmarterMail system administrator can create a custom spam rule for the sending domain that artificially removes any negative spam score. That way, emails from VeryImportantClientDomain.net don't end up in the Junk Email folders of BestAZLawFirm.com users.
To configure weights for custom rules, click New, then complete the following fields:
- Rule Name - The name of the rule.
- Rule Source - What you want the rule to be based on: a message's header, body text or raw content. When selecting "body text" or "raw content", you'll need to supply additional information that is applied to the Rule Text: whether the Source "contains" the information, whether the wildcard is used for a range of information or whether you want to supply a regular expression. If you select Header you will need to supply header details separately from the Rule Text.
- Rule Text - The text that will be used in conjunction with the Rule Source. For example, if you use create a Rule Source based on Body, then an additional Rule Source for "Contains", Rule Text can include words such as "Cialis", "Viagra", "male enhancement", etc.
- Weight - The amount to add to the email message's spam weight.
- Match Multiple - Enabling this allows the spam weight calculated for the rule to increase based on
multiple instances of the Rule Text that's added. In general, a custom spam check based on any Rule Source will
check for the FIRST instance of a word or phrase that's been added to the Rule Text and apply that weight. It
doesn't matter if all of the words or phrases are found — only the FIRST instance is counted and the weight
applied. When Match Multiple is enabled, the first instance of ALL words or phrases in the Rule Source is
counted and the total score is used.
Note: when using Body as the Rule Source, the spam check looks at both the HTML and plain text versions of a message, primarily because these versions may differ in content. As a result, the total weight may vary.
- Enable Spool Filtering - When enabled, the weight assigned for the spam check is added to the message and used as part of its overall spam score. SmarterMail then handles the message based on the spam settings configured for a domain.
- Enable Outbound SMTP Blocking - See above for details.
Match Multiple Examples
The concept of the Match Multiple settings can get a bit confusing. Below are a couple of examples of how Match Multiple works.
Rule Source: Header
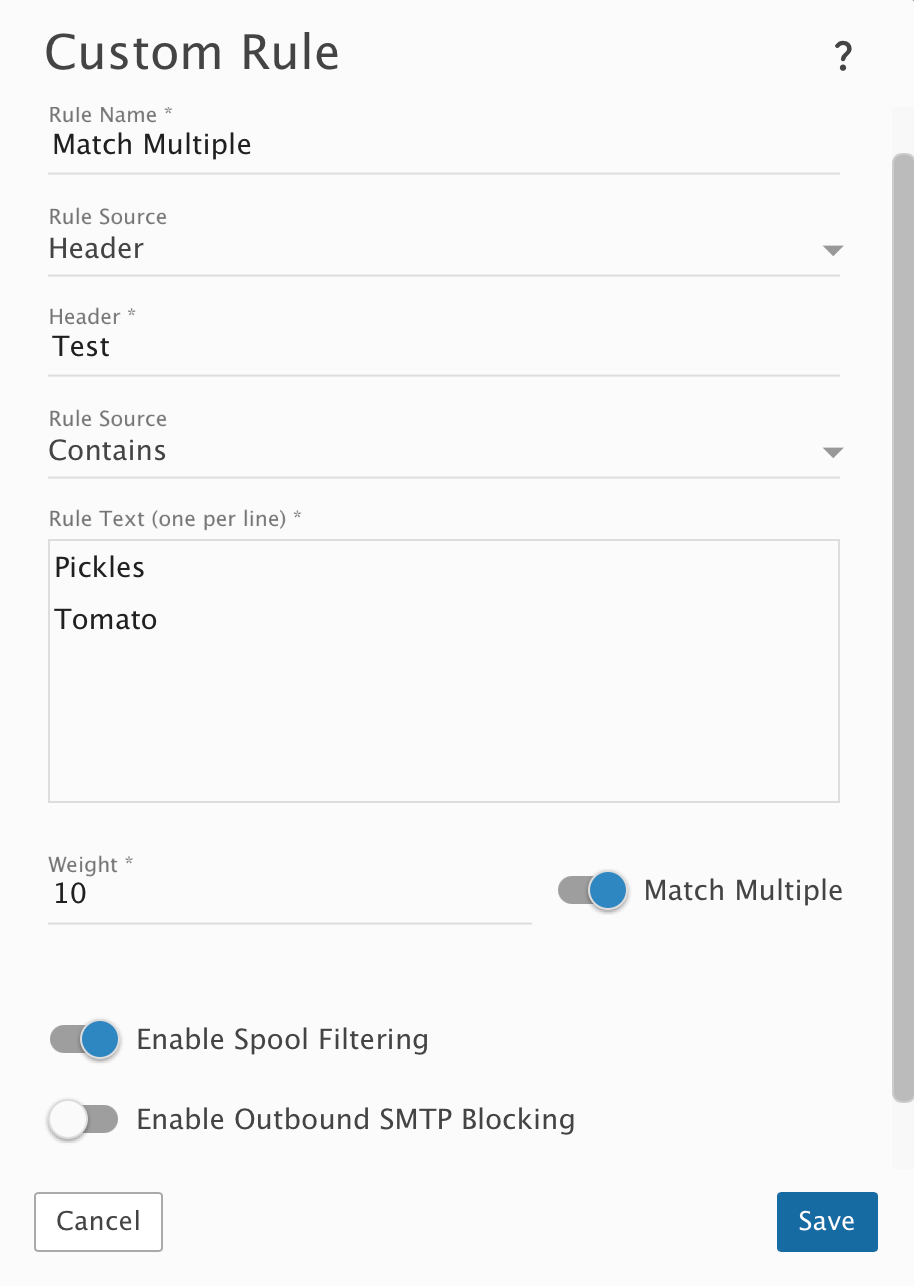
- An incoming email that contains two separate headers of "Test: Pickles" will get a weight of 20 for this spam check. ("Pickles" in the first header will trigger a weight of 10, and "Pickles" in the second header will trigger a weight of 10.)
- An incoming email that contains a single header of "Test: Pickles Pickles" will get a weight of 10 for this spam check. (The first instance of "Pickles" in the header will trigger a weight of 10.)
- An incoming email that contains a header of "Test: Pickles Pickles" and a header of "Test: Tomato" will get a weight of 20 for this spam check. (The first instance of "Pickles" in the first header will trigger a weight of 10, and the instance of "Tomato" in the second header will trigger a weight of 10.)
Rule Source: Body
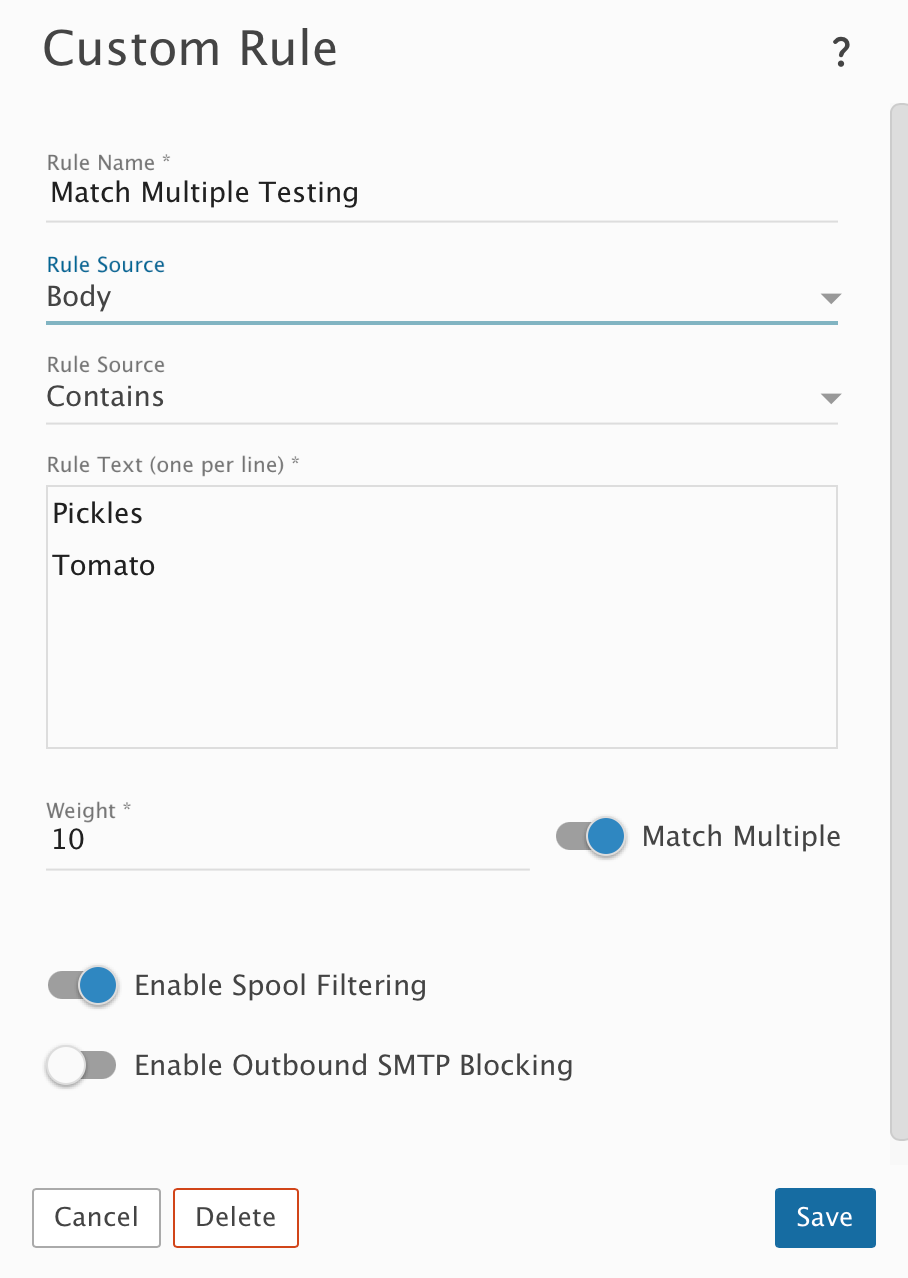
- An incoming HTML + plain text email that contains "Pickles Tomato" in the message body will get a weight of 40 for this spam check. ("Pickles" in the HTML content will trigger a weight of 10, "Pickles" in the plain text content will trigger a weight of 10, "Tomato" in the HTML content will trigger a weight of 10, and "Tomato" in the plain text content will trigger a weight of 10.)
- An incoming HTML + plain text email that contains"Pickles Pickles Tomato Tomato" in the body will get a weight of 40 for this spam check. (Only the first instance of the Rule Text words in the HTML content and plain text content will trigger the weight.)
- An incoming plain text only email that contains "Pickles Tomato" in the body will get a weight of 20 for this spam check. ("Pickles" in the plain text will trigger a weight of 10, and "Tomato" in the plain text will trigger a weight of 10.)